According to DeFillama, the TVL in DeFi is currently around $124.5 billion. However, in early 2022, that figure reached $240 billion. One way or another, we’re talking a lot of money. There is, however, one thing that can throw a spanner in this DeFi machinery. These are bugs in the smart contracts.
With so much money at stake, you expect projects to prepare themselves. Well, some do this better than others. Ken Deeter, a Twitter investor, and builder wrote a thread on this. He mentions five security practices you need to look for when doing your own research (DYOR). Let’s have a look at what these practices in smart contracts are.
0/ With $220B of TVL on the line, bugs in smart contracts are one of the biggest challenges in DeFi.
Some projects are way more prepared than others when it comes to protecting their users.
🧵 Here are 5 security practices you should look for when sizing up a project.
— Ken Deeter ve(⚡️) (@puntium) April 12, 2022
What Are 5 Good Security Practices for Smart Contracts?
When you start doing your own research, you need to tick these five boxes off the list. They will reduce the possibilities of a smart contract hack. So, let’s take a deeper look into each of them:
1. Bug Bounties
Bug bounties are something that projects offer, so people find bugs and report them. In return, they earn a bounty. This is in contrast to exploiting a bug. For instance, protocols, exchanges (CEXs and DEXs), or wallet operators can offer bounties.
A variety of platforms specialize in giving a helping hand to bounty finders. For instance:
- Immunefi: They organized over $128 million in rewards so far. They prevented $20 billion in damages.
- Lossless: They put a simple piece of code in token contracts. Once somebody spots suspicious activities in a transaction, they can freeze the transaction. The ‘spotter’ earns a reward in case something was not kosher in that transaction.
Dopex has launched their bug bounty on Immunefi 💪@dopex_io decentralized options protocol aiming to maximize liquidity, minimize losses for option writers and maximize gains for option buyers
Find those bugs 🔍 – get yourself a sweet $444,444:https://t.co/g0OCBKLTbb
— Immunefi (@immunefi) May 25, 2022
2. Formal Verification
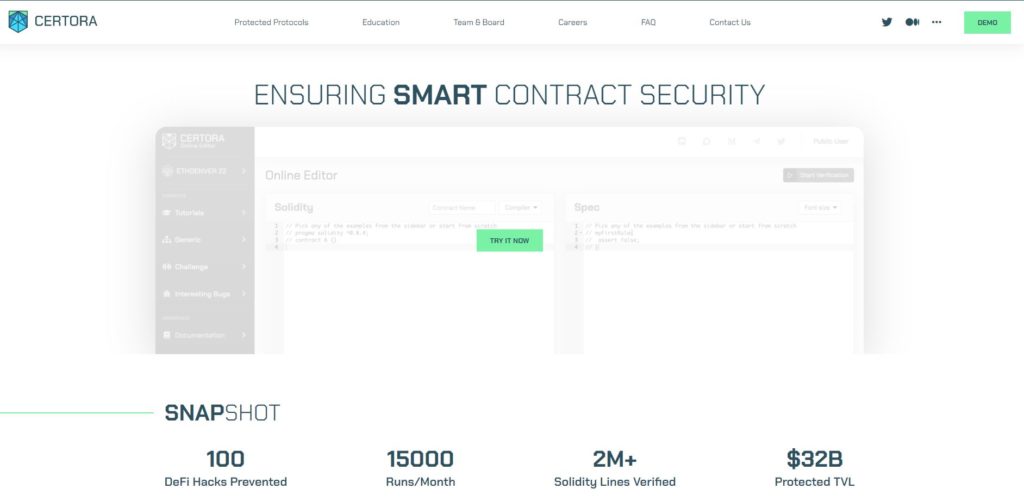
A company like Certora checks code correctness in smart contracts. The list of protocols that use their service seems endless. Plenty of well-known names among them as well. For example, Aave, Compound, or Balancer. At the time of writing this article, they claim to have prevented 100 hacks. They also protected $32 billion in TVL.
Source: Certora
3. Risk Markets
It is possible to price and trade smart contract risks. There are a few protocols that pioneer this market-based approach. For example, Nexus Mutual. They offer coverage against smart contract failure and exchange hacks. In the same vein, Cozy Finance or Sherlock DeFi offer similar protection.
The participating protocols protect their users by integrating their market into the applications.
Introducing Cozy Invest
🚀 Invest in one click
🪙 Earn and manage reward tokens
🛡 Protection, when you need itAll in one place. Try it out at https://t.co/88zL39e2ji. pic.twitter.com/A3aIisbAhn
— Cozy Finance 🦥 (@cozyfinance) November 3, 2021
4. Audits
Having your protocol audited is still a big deal in crypto and DeFi. However, there’s also a lot of time stress in DeFi. As a result, many protocols don’t always take the time to have their smart contracts audited. This makes these non-audited protocols prone to hacks.
However, audits really seem to be the least a project should have in place for protection. To clarify, once a protocol updates or changes its code, it needs a new audit. Hacken, OpenZeppelin, and Certik are well-known crypto audit firms. Keep in mind that an audit is no guarantee that a protocol won’t get hacked.
Congrats to Skynet partner @Nodereal_io 🤝
We are excited on Skynet’s integration with Nodereal to enable on-chain #Web3 security monitoring and data analytics services. See Skynet in action 👉 https://t.co/EG9dTAefGj https://t.co/0yqHSV5FGN
— CertiK (@CertiK) May 18, 2022
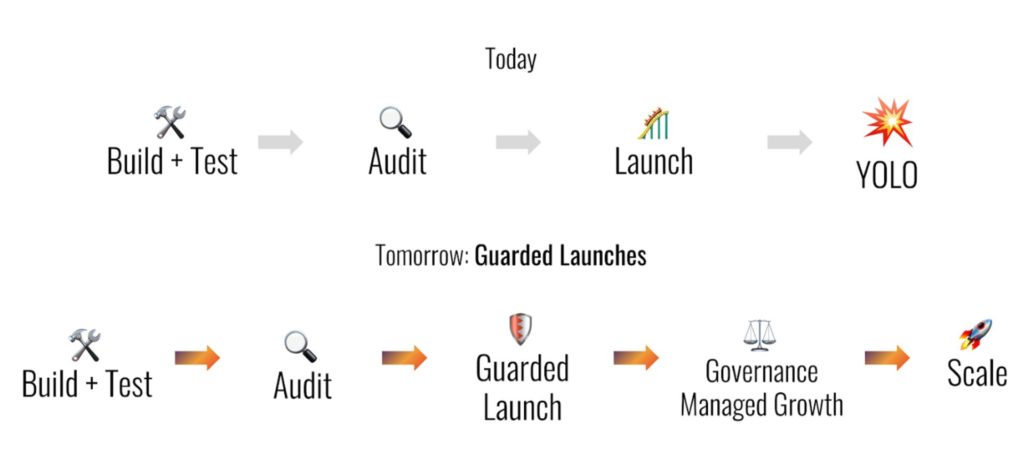
5. Guarded Launches
This means that when projects launch, they limit the number of users allowed on the platform. This way, they limit the assets put at risk. Do some more research, for instance, by looking at older blog posts. They will tell you how they dealt with their launch.
Source: Medium
Conclusion
It is almost a given that developers write buggy code. However, what is of importance is how they try to catch the bugs and protect the protocol. This is the difference that will set safer protocols apart from less-safe ones. We showed you five practices that you should look for when you DYOR on DeFi protocols.
⬆️For more cryptocurrency news, check out the Altcoin Buzz YouTube channel.
⬆️Find the most undervalued gems, up-to-date research, and NFT buys with Altcoin Buzz Access. Join us for $99 per month now.