Smart Contracts are the backbone of blockchain. These contracts ensure that we do not need to trust a 3rd party. Top De-Fi smart contracts lock of over $10 Bn in Total Value. The launchpads distribute tokens of IDO projects through smart contracts. But can you trust the code? Let’s see what ConsenSys has to say on the subject.
On December 5th, crypto exchange Bitmart suffered a huge hack of $196 Million.
The hackers were able to extract assets from 2 of the exchange’s hot wallets. Previously on August, 17th, Poly Network suffered one of the biggest hacks in the history of cryptocurrencies. $600 Million worth of tokens was hacked from the De-Fi protocol.
In fact, the alarming conclusion from both the above examples is that both Centralized and Decentralized Protocols remain vulnerable even after being audited. NCC Group did the protocol audit and CertiK did the Ethereum Smart Contract Audit of Poly Network.
So this raises questions about the poor security practices by the protocols and also the quality of audits conducted. Are the auditors responsible for not finding vulnerabilities?
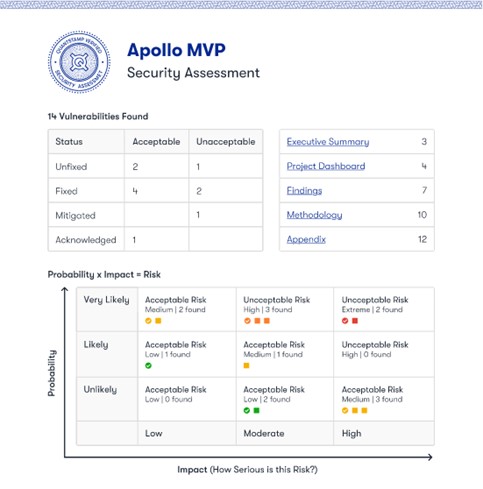
Let’s check out this sample audit report from Quantstamp.
Manual Audits
The Manual Audit of Quantstamp analyzes various parameters and groups them into Unacceptable and Acceptable vulnerabilities. These critical unacceptable vulnerabilities are then put into a framework where they assess their probability of occurrence. Above all, it is up to the protocols to fix the vulnerabilities. Some protocols might decide not to fix some, for example an unlikely vulnerability with a low impact. And this occurs when the vulnerabilities require drastic changes in the protocol and the developers are restricted by strict timelines. So you might have guessed, such trade-offs are one of the major causes of hacks.
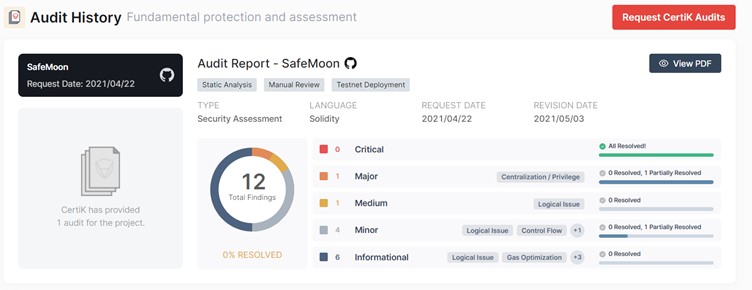
In the below example, Certik conducted an audit for a project called Safemoon. You can see they found 12 vulnerabilities. And Safemoon resolved none of them.
For more, the full report can be downloaded from this link.
Security Monitoring Software
The protocols also implement 24×7 live security monitoring tools. First, these tools scan millions of transactions per day and provide alerts that can include important parameters like
- Flash loan anomalies
- Changes in token supply
- External attacks
- DEX Liquidity issues etc.
Secondly, they provide a quick way to identify hack attempts and fix problems. After all, thousands of attacks occur every day.
But is this enough? Just like the standard protocols, the audit protocols are also shaping up their offerings. Surprisingly, there is no proper standardization. And there’s a lack of a 360-degree (comprehensive) audit methodology.
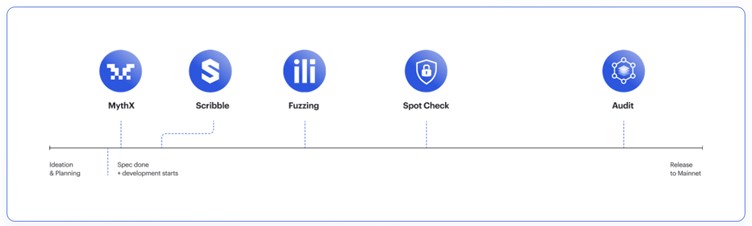
According to the latest quarterly Consensys Web 3 Report, a security product should cover all these bases. In fact, each stage of the delivery cycle should go through audits. This methodology eliminates the current Ad-Hoc security audits that remain erroneous and is the current landscape. Consensys implements security solutions throughout the lifecycle of product development, starting from ideation and planning to Mainnet.
Ideally, the scope of audit now becomes broader and includes:
- Security Layer 1: Find known vulnerabilities. An automated detection system with a huge database of all past exploits should be able to identify the immediate fixes.
- Security Layer 2: Specific to Ethereum, Consensys’s product, Scribble, inserts Solidity assertions to check the protocol. It acts as an extra checkpoint for the test suite.
- Security Layer 3: Continuous checks of the smart contract code, as the developer writes them, using millions of inputs
- Security Layer 4: The manual audit starts after the completion of the first 3 layers (and after a quick Spot Check). This phase is similar to the Quantstamp example explained previously. Notable Auditors include Quantstamp, Certik, Hacken, etc.
- Security Layer 5: 24X7 Security Checks through software should be the final implementation to complete the comprehensive audit.
With better learning and understanding of the various types of vulnerabilities, the systems will mature more and we will be able to detect flaws in Security Layer 1 software. However, this will take time and will be gradual. Remember that we are early adopters. The early stages will always involve risks.
Resources: Consensys Web3 Report Q3 2021
Read More: Test And Review Of The Blank Wallet